Consult the experts, know the risks
A cybersecurity strategy with a difference
The strategic guidance from our team of engineering-led experts will keep cybersecurity central to your operations and digital transformation. Our consulting services can help discover, design, implement, maintain and optimise your IT investments with security always at the forefront.
Governance, Risk and Compliance
Good governance of your cyber resilience is more than just keeping up with industry best practices. Your goal is to reduce exposure to cyber threats, understand your risk position and act upon it.
The damage caused by cyber attacks can be irreversible. Why risk destruction of your intellectual property or a regulatory breach? Any attack can result in serious consequences for your organisation’s operational productivity and reputation.
Our expert team start by listening to your security concerns. Rest assured, at every stage we provide guidance and insight to your compliance progress.
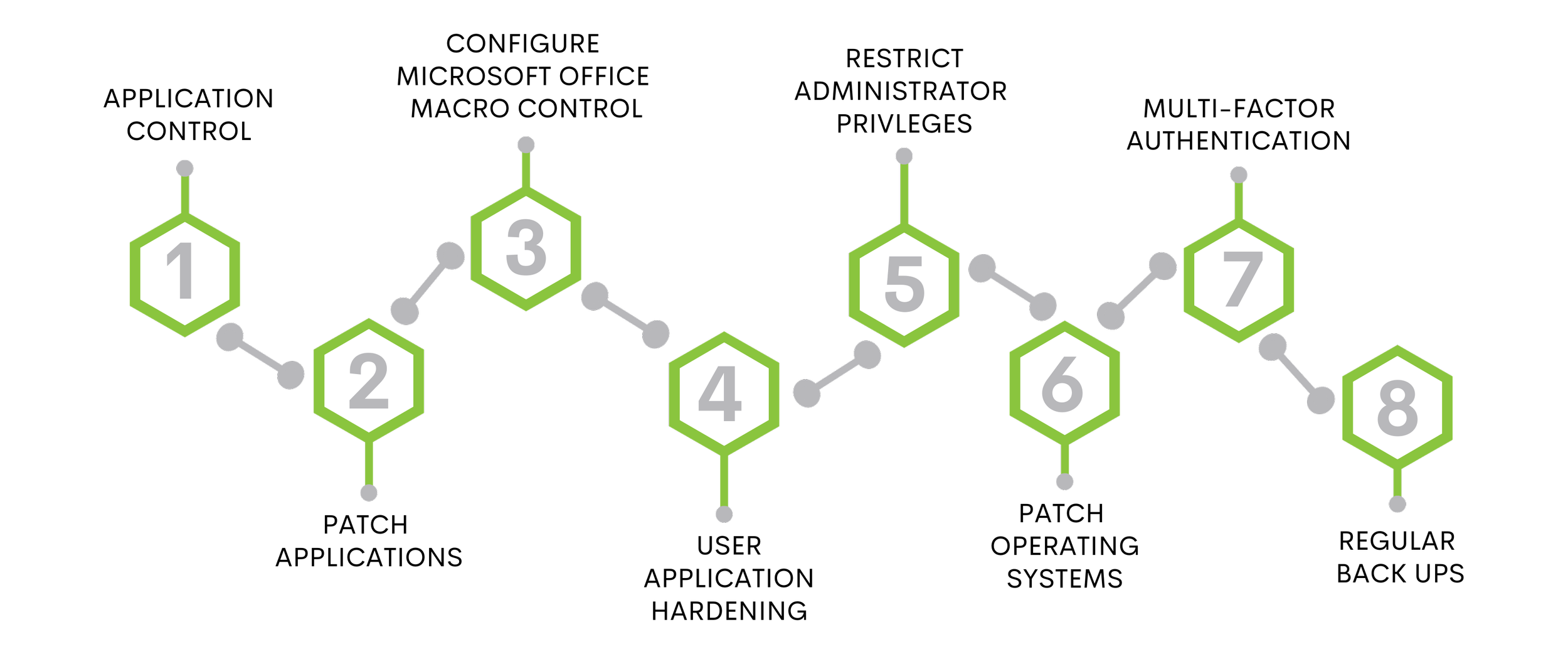
What is the Essential Eight?
The Essential Eight is an Australian cybersecurity framework from the Australian Cyber Security Centre. This set of eight strategies has been designed to enhance the cyber resilience of businesses and government. It is recommended that these strategies are employed by organisations as a baseline for their cybersecurity strategy.
Are you Essential Eight compliant?
Implementing the Essential Eight framework can be a daunting task for organisations. At CBR Cyber, we take a blended approach of consultation and workshopping complemented by a technical deep dive and vulnerability assessment.
We help you set your maturity target strategy and offer a meticulous assessment of your current position. We limit human error and provide value for money through deeper context to the recommendations and maturity roadmap. Finally, we outline a roadmap for implementing these mitigations in your network with our cyber engineering team.
Monitoring your cyber resilience
For many organisations it is a constant challenge to ensure effective security has been maintained. Compounding this issue is the high frequency of vendor updates, meaning newly introduced components are often missed or not utilised to their full extent.
Our cyber health check services asses your security effectiveness and its integration into the network environment. We compare vendor features and recommended practices and combine these with real world experience. We provide recommendations based on findings and prioritise them in a way that can be deployed easily.
Cyber Health Check
-

Privilege Access Management
-

Vulnerability Management
-

Voice, Video and Unified Communication
-

Firewall
-

Application Whitelisting
-

Networking
End-to-end solutions backed by the best technology
Our specialist Architecture and Design services allow organisations to plan and adopt new technologies in a secure and measured way. Our focus is to deliver fit-for-purpose architectures which drive down costs and operational complexity while improving service availability, security, functionality, and performance.
Our team are constantly abreast of evolving technologies and industry trends, ensuring our customers benefit from market-leading solutions that are architected for Federal Government and critical infrastructure use.